If you’ve ever worried about someone breaking into your WordPress dashboard — you’re not alone.
Account takeovers (ATOs) are one of the leading causes of website compromise, and it doesn’t just affect Fortune 500 companies.
In fact, 43% of cyberattacks target small businesses, according to a 2022 report by Verizon.
That includes blogs, eCommerce shops, nonprofits, agencies, and even simple portfolio sites — many of them powered by WordPress.
Real-World Data Breaches Caused by Password Theft:
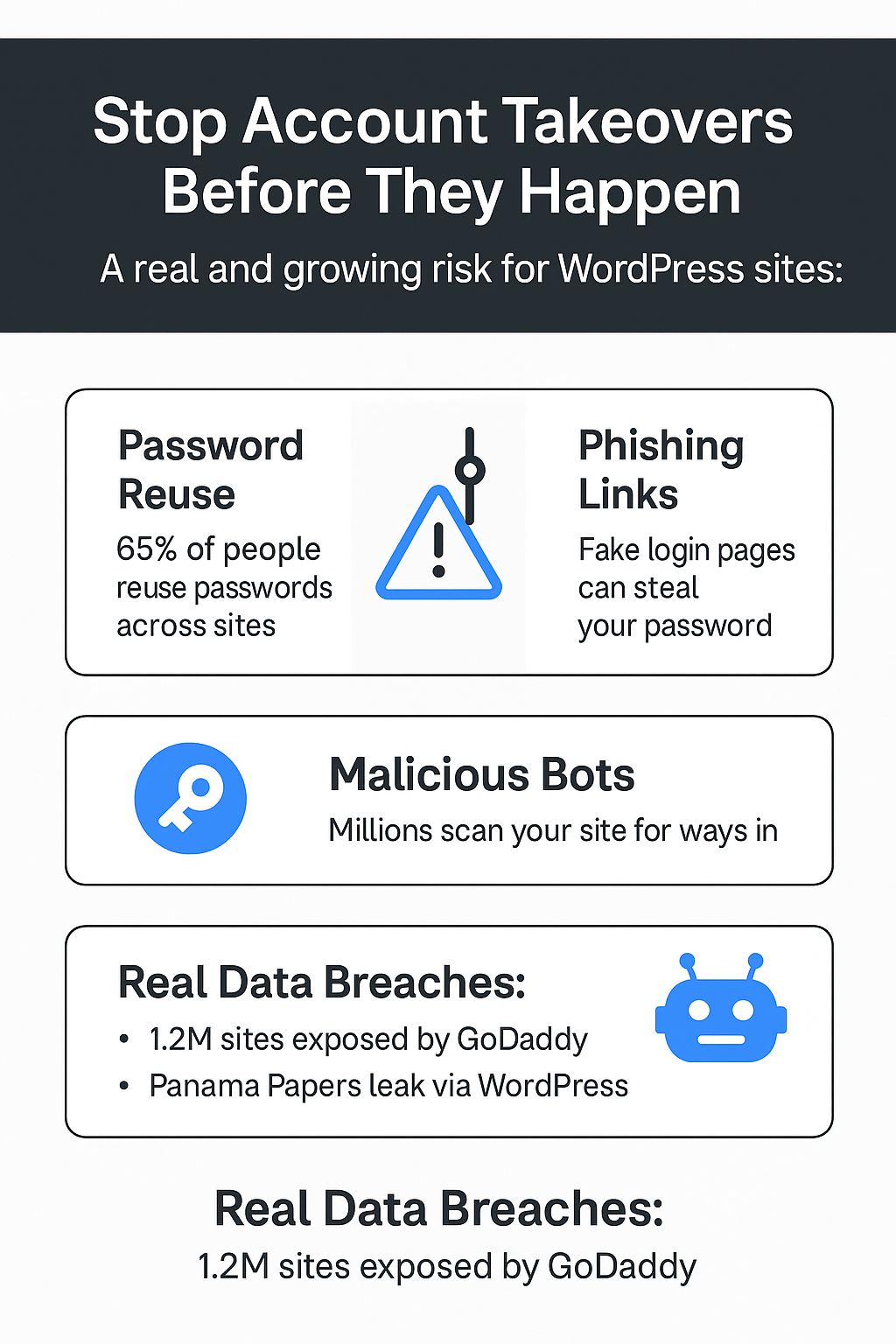
1. GoDaddy WordPress Breach (2021)
1.2 million WordPress sites compromised.
Cause: A compromised password allowed attackers access to hosting accounts.
2. Panama Papers Leak (2016)
One of the largest data leaks in history.
Cause: Outdated WordPress plugin + weak password on a WordPress admin panel.
3. Zerodium Exploit (2020)
Zero-day exploit affecting WordPress core login process.
Used in combination with phishing and brute force tools to hijack dashboards.
Why This Problem Is Bigger Than You Think
Here’s what’s happening right now:
🚨 Problem #1: Password Reuse Is Rampant
Studies show 65% of people reuse passwords across multiple accounts.
So when one site gets breached (like LinkedIn, Facebook, or Dropbox), attackers try the same login details on your WordPress site.
🔓 Example: A reused password from a 2012 Dropbox breach is still used by users today. Hackers feed these into bots to try on login pages.
🚨 Problem #2: Phishing Is Getting Smarter
Attackers create fake WordPress login pages that look identical to yours. You click, you type your password — they steal it instantly.
🎣 Phishing kits are now sold as low-cost subscriptions on dark web marketplaces, targeting WordPress and WooCommerce site owners.
🚨 Problem #3: Bots Don’t Sleep
Millions of bots scan WordPress login pages daily using credential stuffing (trying email + password combos) or brute force (testing thousands of combinations).
🤖 On average, Wordfence logs over 100 million blocked login attempts per day across WordPress sites.
❌ What Current MFA Plugins Miss
Even with 2FA plugins:
Users forget codes or ignore MFA prompts.
Attackers intercept SMS codes or hijack sessions.
Many plugins don’t protect against reused or phished passwords.
🧠 Why We Built A1Auth
We knew site owners needed something better — so we created A1Auth, the first visual MFA solution for WordPress that adds a style and character-layered defense to every login.
Even if your password is leaked… Even if bots guess the characters… They still can’t replicate your visual login signature.
So What Happens When You Use A1Auth?
You stop worrying about password leaks
Bots bounce off your login page
Users stop complaining about confusing MFA codes
You’re actually ahead of compliance rules like HIPAA and GDPR
🔒 Ready to Lock Down Your Site?
If you’ve got a WordPress site, and you care about keeping control of it — it’s time to upgrade your login.
With A1Auth, you get smarter security that users don’t hate.
No more panic when someone says, “I think I got phished.”
👉 Start Free Now